How to: Multi-Factor Authentication, Office 365 and Server 2012 R2 ADFS v3.0 - Part 1
A series on certificate based authentication.
This is part 1 of a series I’m putting together around Multi-Factor Authentication (MFA). Recently I’m been working with a client on a project to implement MFA for Office 365 services as company policy mandates at least two factors of authentication (2FA) for accessing any corporate resources.
In part one I’ll put together my points of view around what MFA is, why its an important topic for organizations especially in 2015. In part two I’ll explain what the main MFA types are around Office 365 and Azure and their use cases as each has different features and each can impact different aspects of implementations. In part three I’ll explain how to implement MFA in organizations that utilise ADFSv3.0 integration with Office 365, and finally in part four provide an in depth how to for the latest currently “in preview” feature of Microsoft Office 2013- MFA utilising Active Directory Authentication Library (ADAL) that was only made available for preview in Q4 of 2014. This is exciting cutting edge stuff that will no doubt be a standard configuration item for existing and new Office 365 customers by the end of 2015.
Lets kick things off with the background of MFA and set the foundations of the posts to come…
What is multi-factor authentication (MFA)?
Multi-factor authentication (MFA) is a means of access control whereby during the logon process, there is more than one claim to grant you access to the cloud service, server application or even workstation.
What this means in a nutshell is when you logon to your Office 365 Outlook Web Mail web client, along with your username and password combination (something you know), you are required to also enter an additional means of authentication like a one time token (OTT) (something you have).
To finally expand upon that, we have the most basic of MFA concepts where everything can be summed up in three key scenarios of something you know, something you have and finally something you are. This philosophy of authentication ensures that its virtually impossible to beat the system when up to all 3 factors are enabled.
Why does it matter to my organization?
More and more organizations are moving to the cloud. Key services like email through to line of business applications used by accounting are ending up in a cloud. With that comes some risk; of data being compromised and ever more likely: user credentials being compromised. Systems able to be implemented like CloudLink SecureVSA, available in Microsoft Azure, keeps data at rest encrypted and secure, meaning not any old user can access raw data and compromise corporate intellectual property. The most common way to compromise applications, cloud services or systems as I mentioned earlier is through user credentials. Your username and password have kept your work and your access to systems and applications secure for the most part since the invention of computer systems.
Fast forward through to modern day cloud centric IT. A world where you have an increasing amount of the workforce using any number of cloud service or cloud application. For the security conscious and those in the positions to make the decisions to keep the rest of the organisation secure, this was a headache. I say was because with an ever growing number of cloud users, cloud providers are coming up with better ways to secure thier services. In some ways Microsoft are leading the charge. Of Course other providers like Amazon Web Services (AWS) have MFA services of their own, the potential of MFA use in both Microsoft’s Office 365 and soon Office 2013 has much greater impact.
Why is 2015 going to be a big year for MFA?
Through various reading, Googling and background I have on the subject matter, it seems to me that coming off some strong development work in 2013 and 2014, the year 2015 will be the year that MFA goes mainstream: beyond just securing your bank account (through the use of SMS one time pass-codes (OTP)) and into virtually all enterprise and even standard cloud services as well as thick applications like Microsoft Office.
By far the most popular enterprise and business operating system is Microsoft Windows. Then the most popular workforce application suites are found in the Microsoft Office product stack. Why are these relevant in the cloud world and in the year 2015? Well, put simply, both are from Microsoft and both will feature strong MFA functionality with integration to key cloud services, again from Microsoft, Azure and Office 365.
Microsoft Windows 10
Microsoft announced that Windows 10 will tie in with Azure Active Directory (AAD) allowing for organizations to be born in the cloud. This is big news especially in relation to MFA where Windows 10 will be the first operating system to feature MFA integration. This point isn’t that much of a talking point in this series, but definitely one of the reasons why 2015 is going to be a big year for MFA. Its something I’m definitely going to get stuck into once Windows 10 becomes generally available.
Microsoft Office 2013
Announced by Microsoft almost a year ago but not able to be publicly used or tested until late 2014, the Microsoft Office 2013 suite will feature MFA integration very soon. Currently available through the connect.microsoft.com in preview testing service, MFA in Office 2013 will likely be many organizations first step towards widespread MFA adoption.
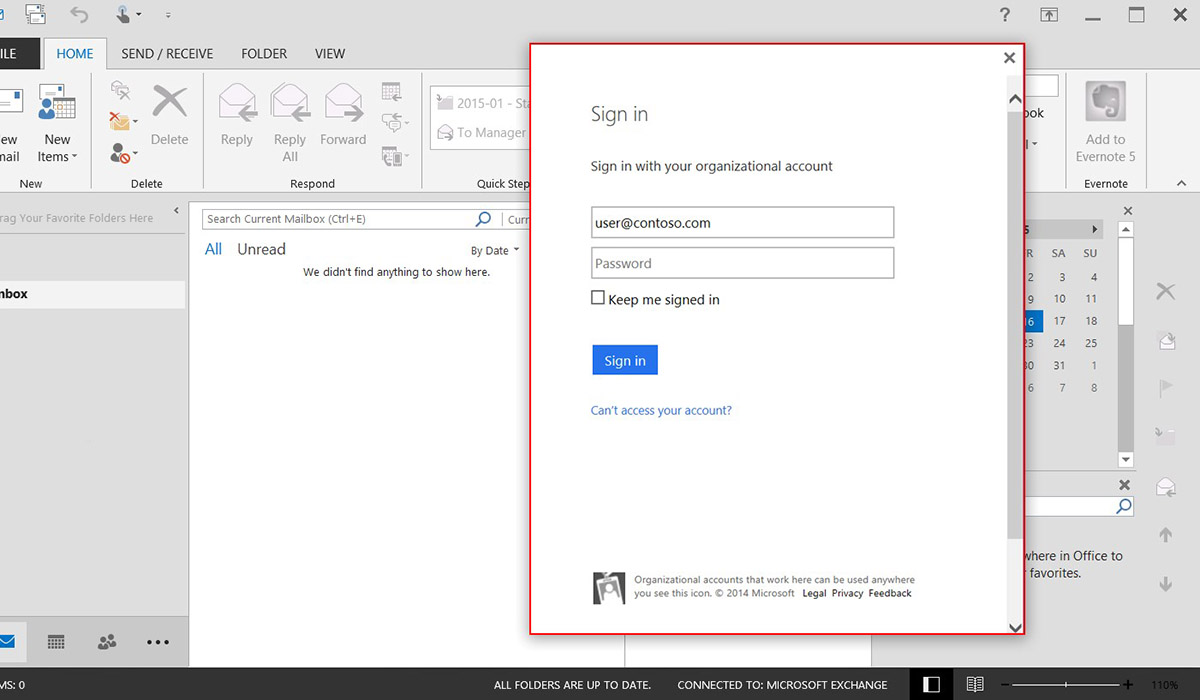
The MFA integration of the Office 2013 suite centres around some key applications that will either talk to ADFS or Azure AD/Office 365: Microsoft Outlook, One Drive for Business and of course Lync. The process itself enables the Office 2013 clients to engage in browser-based authentication (also known as passive authentication). Again put simply, an authentication window will pop up during the logon process requiring the user to enter in additional authentication mechanisms that you as an administrators set.
Exciting reading
For now this makes for some exciting reading as there is huge potential to really secure your Office 365 and Azure AD environments to the maximum. I’m eager to get writing and post the follow up to this post in the series and go into the three key types of MFA options: ADFSv3.0, Office 365 and Azure AD.